1 A DISTRIBUTED CHANNEL ACCESS PROTOCOL FOR AD

1 A DISTRIBUTED CHANNEL ACCESS PROTOCOL FOR AD HOC NETWORKS WITH FEEDBACK POWER CONTROL S. Hasan Raza Naqvi and L. M. Patnaik, Fellow, IEEE TRANSACTIONS ON MOBILE COMPUTING, OCTOBER 2006 Speaker: Han-Tien Chang
Outline 2 Introduction System Model and Related Works Distributed Channel Access Protocol Performance Analysis Performance Evaluation Conclusions Comments
![Introduction 3 Considering power as one of the critical resources in the network [13] Introduction 3 Considering power as one of the critical resources in the network [13]](http://slidetodoc.com/presentation_image_h2/2a60ab67657498e5eba532a2cc7914c1/image-3.jpg)
Introduction 3 Considering power as one of the critical resources in the network [13] The policies for distributed allocation of power are classified as incremental or global Incremental: It allocates the power to the incoming links without adjusting the power of the existing links Global: The power to the incoming link is allocated by adjusting the power of the existing links and, thus, the admissibility of the incoming link is decided globally [13] S. Lal and E. S. Sousa, “Distributed Resource Allocation for DSCDMA Based Multimedia Ad Hoc Wireless LANs, ” IEEE J. Selected Areas in Comm. , vol. 17, no. 5, pp. 947 -967, May 1999.
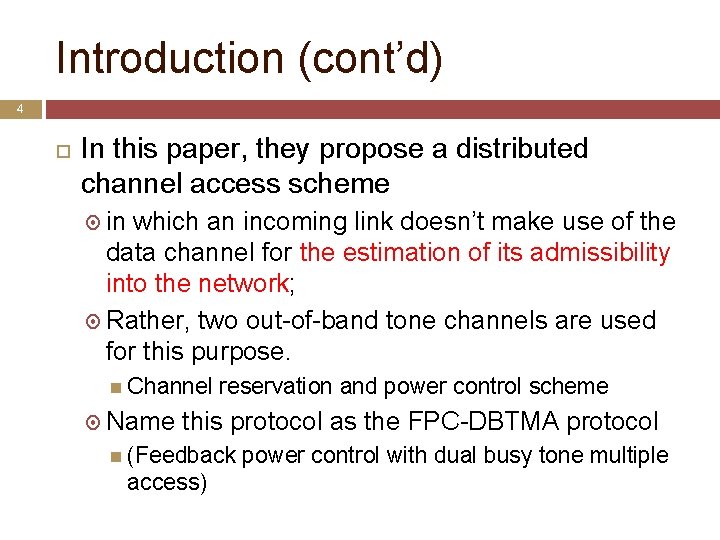
Introduction (cont’d) 4 In this paper, they propose a distributed channel access scheme in which an incoming link doesn’t make use of the data channel for the estimation of its admissibility into the network; Rather, two out-of-band tone channels are used for this purpose. Channel Name reservation and power control scheme this protocol as the FPC-DBTMA protocol (Feedback access) power control with dual busy tone multiple
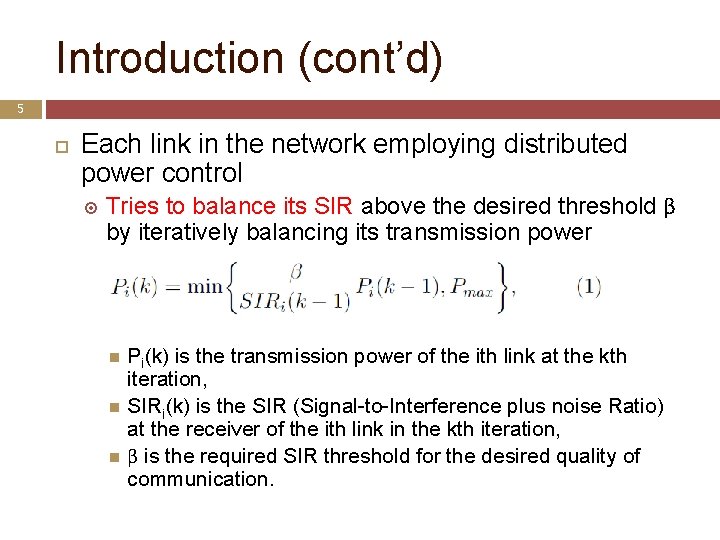
Introduction (cont’d) 5 Each link in the network employing distributed power control Tries to balance its SIR above the desired threshold β by iteratively balancing its transmission power Pi(k) is the transmission power of the ith link at the kth iteration, SIRi(k) is the SIR (Signal-to-Interference plus noise Ratio) at the receiver of the ith link in the kth iteration, β is the required SIR threshold for the desired quality of communication.
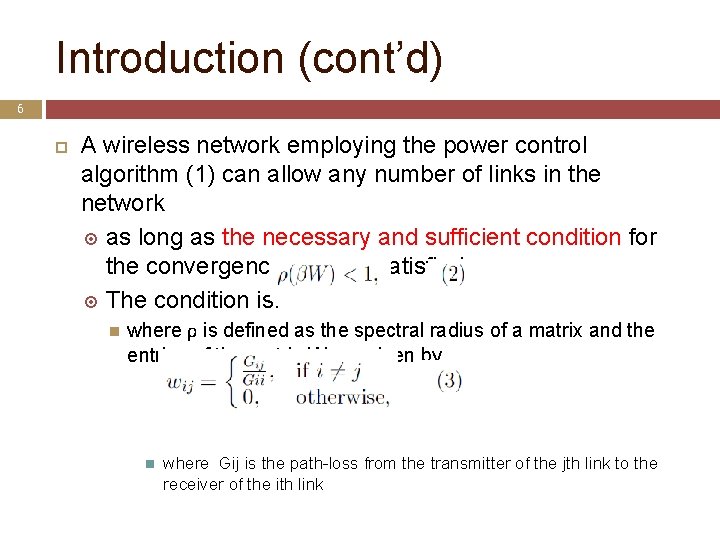
Introduction (cont’d) 6 A wireless network employing the power control algorithm (1) can allow any number of links in the network as long as the necessary and sufficient condition for the convergence of (1) is satisfied The condition is: where ρ is defined as the spectral radius of a matrix and the entries of the matrix W are given by where Gij is the path-loss from the transmitter of the jth link to the receiver of the ith link
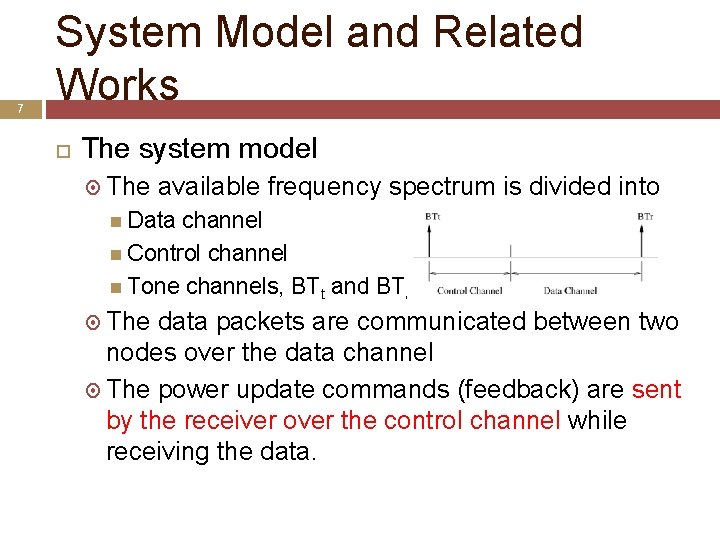
7 System Model and Related Works The system model The available frequency spectrum is divided into Data channel Control channel Tone channels, BTt and BTr The data packets are communicated between two nodes over the data channel The power update commands (feedback) are sent by the receiver over the control channel while receiving the data.

System Model and Related Works (cont’d) 8 The busy channel signals Two out-of-band busy tone channels, BTt and BTr, are used by the links which are trying to access or are accessing the data channel. The role of the BTr signals is to control the admission of the incoming transmitters in the neighborhood of an active receiver whereas BTt signals which are sent by the active transmitters in the network provide the knowledge of admissibility to the receivers of the incoming links
System Model and Related Works (cont’d) 9 Related Works PCMA (Power Controlled Multiple Access) [15] protocol The receiver of each link preserves the interference margin to compensate for the extra interference that will be created by the links joining the network in the future. Thereafter, each receiver in the network transmits busy tone signals, with the power level inversely related to the leftover interference margin, to restrict the admission of the new links in the neighborhood [15] J. P. Monks, V. Bharghavan, and W. -m. W. Hwu, “A Power Controlled Multiple Access Protocol for Wireless Packet Networks, ” Proc. IEEE INFOCOM, no. 1, pp. 219 -228, Apr. 2001. [22] C. Zhu and S. Corson, “A Distributed Channel Probing Scheme for Wireless Networks, ” Proc. IEEE INFOCOM, vol. 1, pp. 403 -411, 2001. Channel Probing Scheme [22]
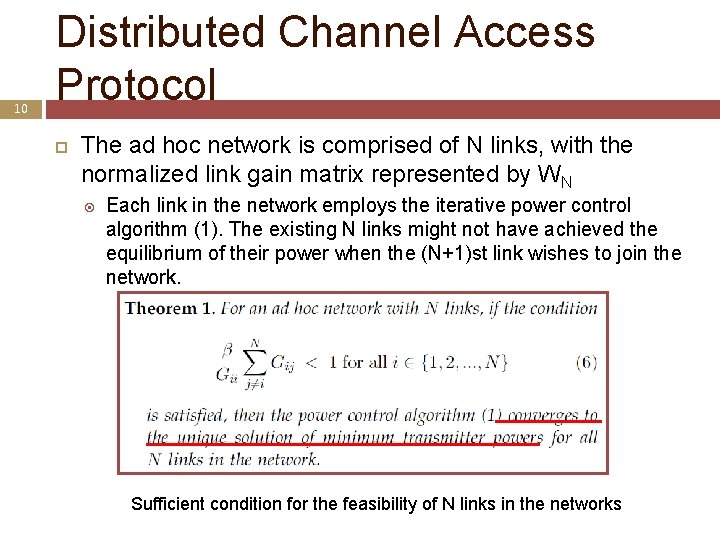
10 Distributed Channel Access Protocol The ad hoc network is comprised of N links, with the normalized link gain matrix represented by WN Each link in the network employs the iterative power control algorithm (1). The existing N links might not have achieved the equilibrium of their power when the (N+1)st link wishes to join the network. Sufficient condition for the feasibility of N links in the networks
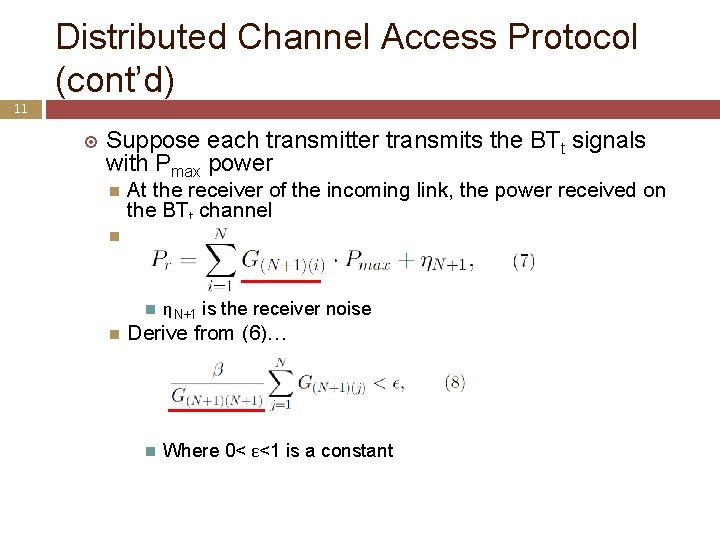
Distributed Channel Access Protocol (cont’d) 11 Suppose each transmitter transmits the BTt signals with Pmax power At the receiver of the incoming link, the power received on the BTt channel ηN+1 is the receiver noise Derive from (6)… Where 0< ε<1 is a constant
Distributed Channel Access Protocol (cont’d) 12 Once the receiver finds itself admissible into the network The receiver (N+1) turns on its BTr signal with a power inversely related to the extra tolerable normalized path -gain component, (1 - ε)
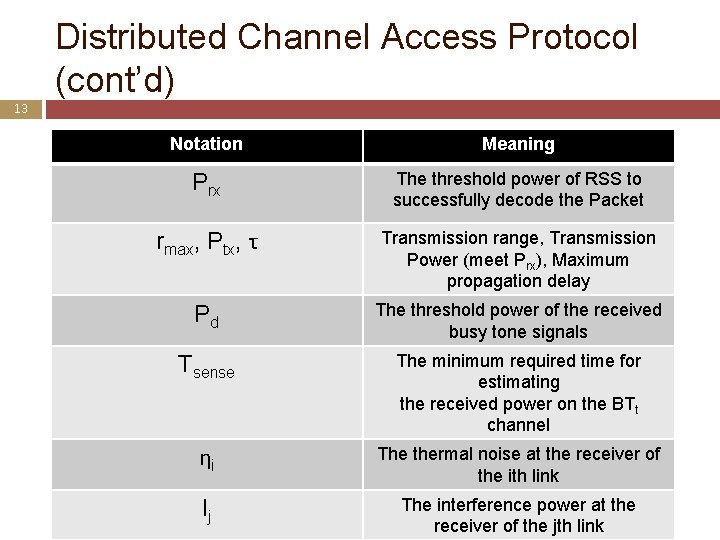
Distributed Channel Access Protocol (cont’d) 13 Notation Meaning Prx The threshold power of RSS to successfully decode the Packet rmax, Ptx, τ Transmission range, Transmission Power (meet Prx), Maximum propagation delay Pd The threshold power of the received busy tone signals Tsense The minimum required time for estimating the received power on the BTt channel ηi The thermal noise at the receiver of the ith link Ij The interference power at the receiver of the jth link
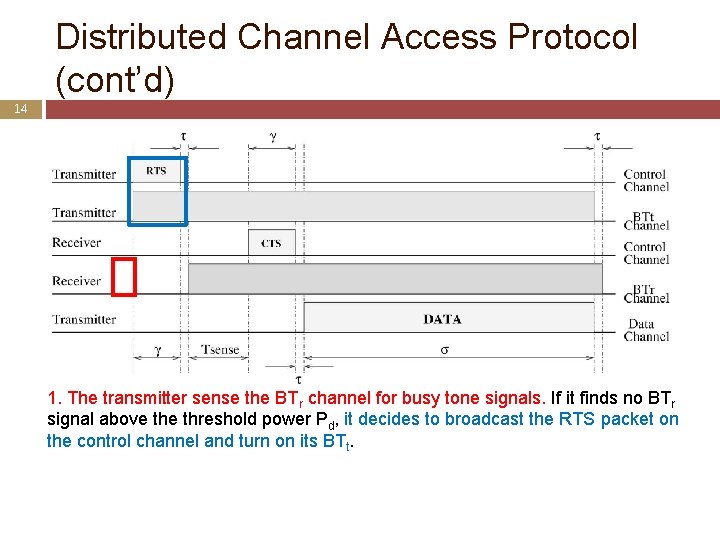
Distributed Channel Access Protocol (cont’d) 14 1. The transmitter sense the BTr channel for busy tone signals. If it finds no BTr signal above threshold power Pd, it decides to broadcast the RTS packet on the control channel and turn on its BTt.
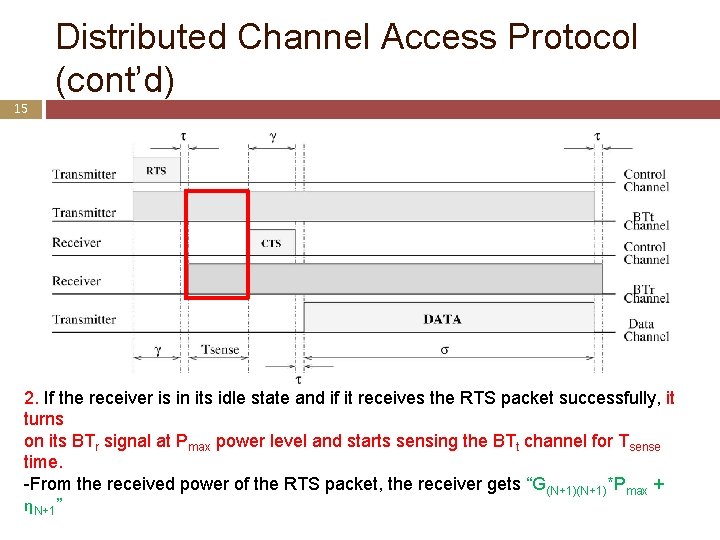
Distributed Channel Access Protocol (cont’d) 15 2. If the receiver is in its idle state and if it receives the RTS packet successfully, it turns on its BTr signal at Pmax power level and starts sensing the BTt channel for Tsense time. -From the received power of the RTS packet, the receiver gets “G(N+1)*Pmax + ηN+1”
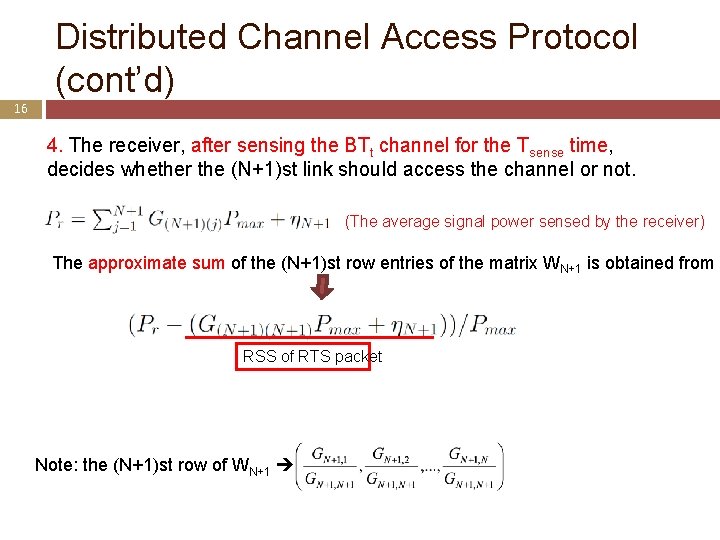
Distributed Channel Access Protocol (cont’d) 16 4. The receiver, after sensing the BTt channel for the Tsense time, decides whether the (N+1)st link should access the channel or not. (The average signal power sensed by the receiver) The approximate sum of the (N+1)st row entries of the matrix WN+1 is obtained from RSS of RTS packet Note: the (N+1)st row of WN+1
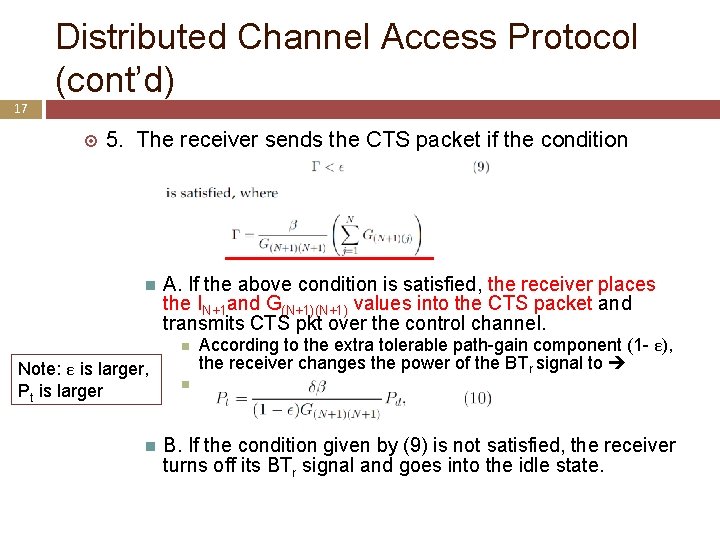
Distributed Channel Access Protocol (cont’d) 17 5. The receiver sends the CTS packet if the condition A. If the above condition is satisfied, the receiver places the IN+1 and G(N+1) values into the CTS packet and transmits CTS pkt over the control channel. Note: ε is larger, Pt is larger According to the extra tolerable path-gain component (1 - ε), the receiver changes the power of the BTr signal to B. If the condition given by (9) is not satisfied, the receiver turns off its BTr signal and goes into the idle state.
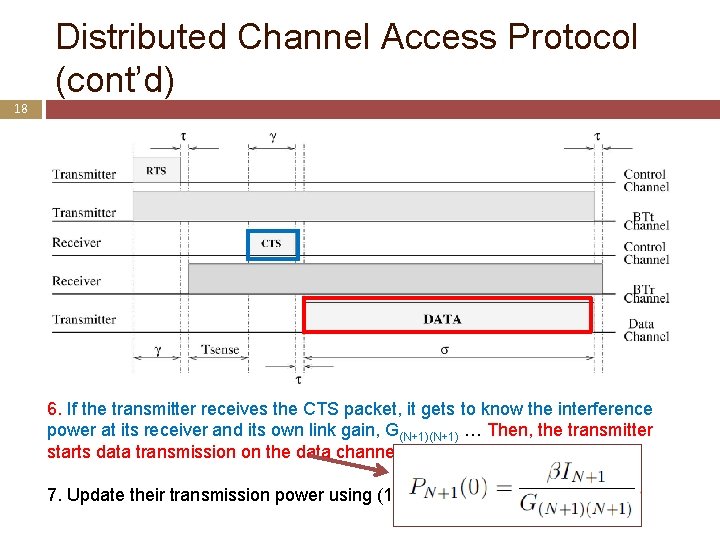
Distributed Channel Access Protocol (cont’d) 18 6. If the transmitter receives the CTS packet, it gets to know the interference power at its receiver and its own link gain, G(N+1) … Then, the transmitter starts data transmission on the data channel with the power 7. Update their transmission power using (1)
Performance Analysis 19 Blocking Probability find the blocking probability of an incoming link as a function of the number of transmitters in the network, the required SIR threshold β and the value of the protocol parameter ε. Average Length of the Admitted Links This introduces a degree of unfairness into the network.
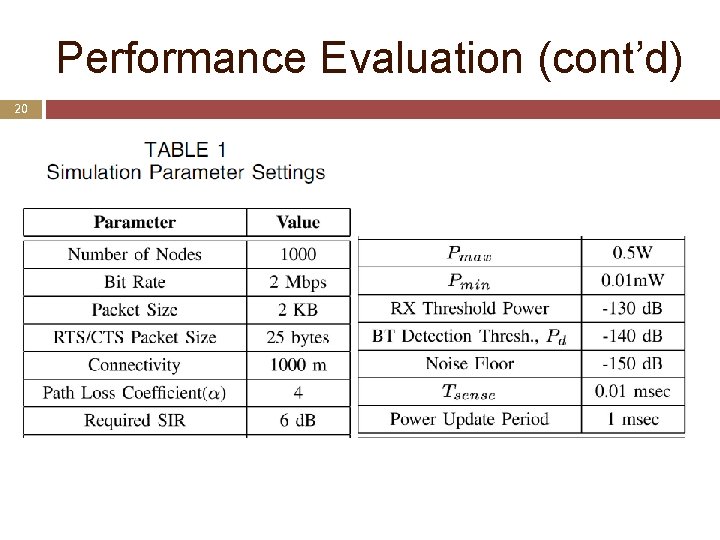
Performance Evaluation (cont’d) 20
Performance Evaluation (cont’d) 21 1. Evaluate the performance of the FPCDBTMA protocol with respect to the number of link drops in the network Compare Distributed Channel Probing Scheme (DCPS) [22] and the FPC-DBTMA scheme
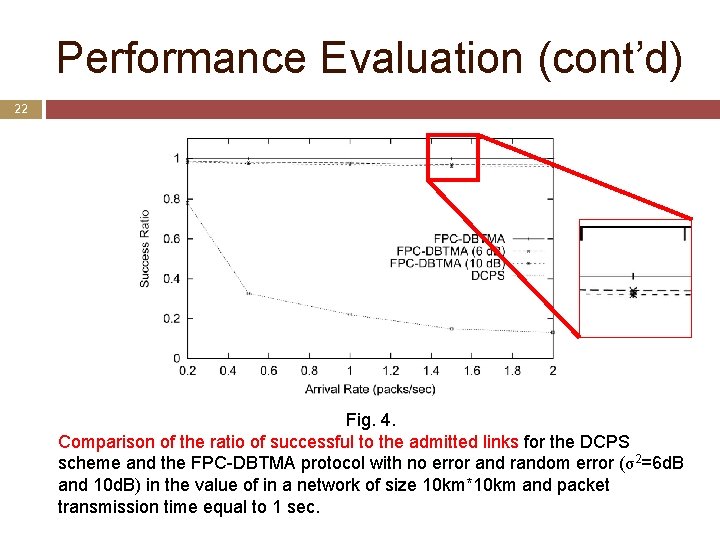
Performance Evaluation (cont’d) 22 Fig. 4. Comparison of the ratio of successful to the admitted links for the DCPS scheme and the FPC-DBTMA protocol with no error and random error (σ2=6 d. B and 10 d. B) in the value of in a network of size 10 km*10 km and packet transmission time equal to 1 sec.
![Performance Evaluation (cont’d) 23 Discussion of evaluation 1 The DCPS [22] scheme suffers from Performance Evaluation (cont’d) 23 Discussion of evaluation 1 The DCPS [22] scheme suffers from](http://slidetodoc.com/presentation_image_h2/2a60ab67657498e5eba532a2cc7914c1/image-23.jpg)
Performance Evaluation (cont’d) 23 Discussion of evaluation 1 The DCPS [22] scheme suffers from a significant number of link drops in the network the success ratio reaches below 0. 2 at a load of 2 packs/sec at each node. The FPC-DBTMA protocol with an accurate estimation of the value of Γ, a success ratio of 1 is achieved the presence of random error for the value of Γ, a success ratio of above 0. 9 is easily achieved under
Performance Evaluation (cont’d) 24 2. Evaluation the channel utilization Calculated as the number of packets successfully received at the network layer per unit time Compare PCMA protocol and FPC-DBTMA protocol Under two different levels of node densities in the network 1000 nodes in 10 km*10 km area 1000 nodes in 20 km*20 km area
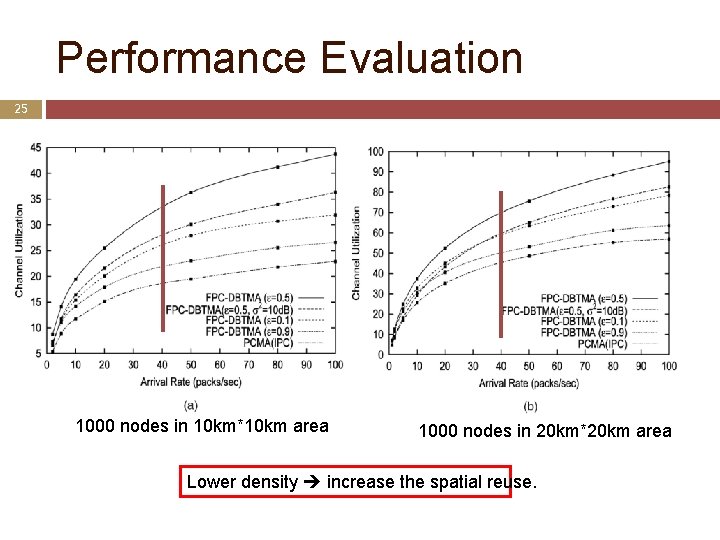
Performance Evaluation 25 1000 nodes in 10 km*10 km area 1000 nodes in 20 km*20 km area Lower density increase the spatial reuse.
Performance Evaluation (cont’d) 26 Discussion of evaluation 2 Even under the presence of random estimation errors for the admissibility condition, The channel utilization for FPC-DBTMA is still higher than that of the PCMA(IPC) protocol. Better channel utilization can be achieved by using the global power control scheme in the network (vs. incremental)
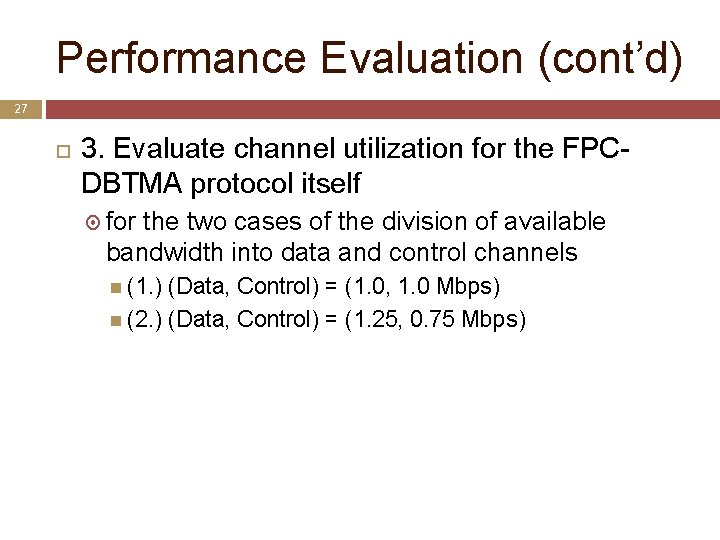
Performance Evaluation (cont’d) 27 3. Evaluate channel utilization for the FPCDBTMA protocol itself for the two cases of the division of available bandwidth into data and control channels (1. ) (Data, Control) = (1. 0, 1. 0 Mbps) (2. ) (Data, Control) = (1. 25, 0. 75 Mbps)
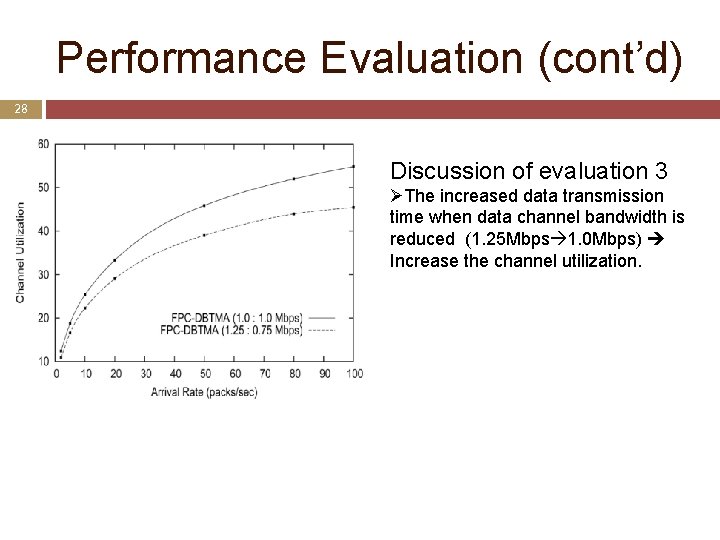
Performance Evaluation (cont’d) 28 Discussion of evaluation 3 ØThe increased data transmission time when data channel bandwidth is reduced (1. 25 Mbps 1. 0 Mbps) Increase the channel utilization.
Performance Evaluation (cont’d) 29 4. Evaluate the maximum capacity of the network Compare concurrent transmissions under different protocol parameter ε From Step 5 of the FPC-DBTMA protocol, a lesser value of ε, the surrounding channel reserved by the receiver of a link is lesser. For
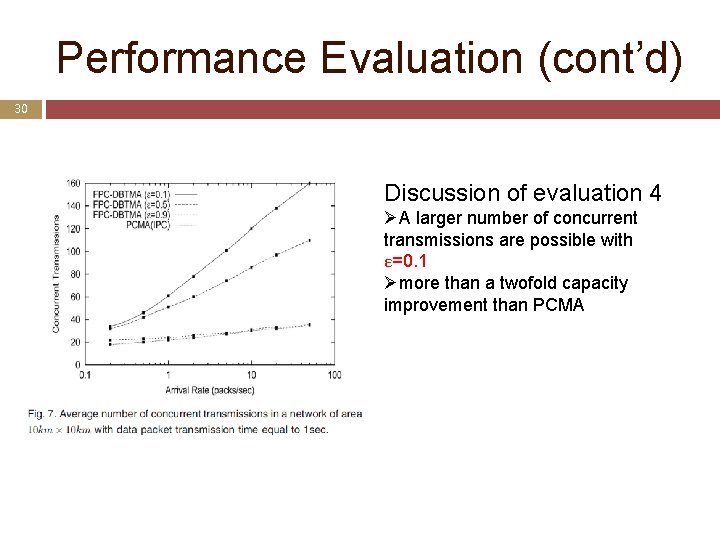
Performance Evaluation (cont’d) 30 Discussion of evaluation 4 ØA larger number of concurrent transmissions are possible with ε=0. 1 Ømore than a twofold capacity improvement than PCMA
Performance Evaluation (cont’d) 31 5. Impact of Mobility The nodes in the network being mobile, the topology of the network changes frequently. Problem!!! The topology change may also introduce instability into the network for the power control to converge, and this may result in a higher number of link drops.
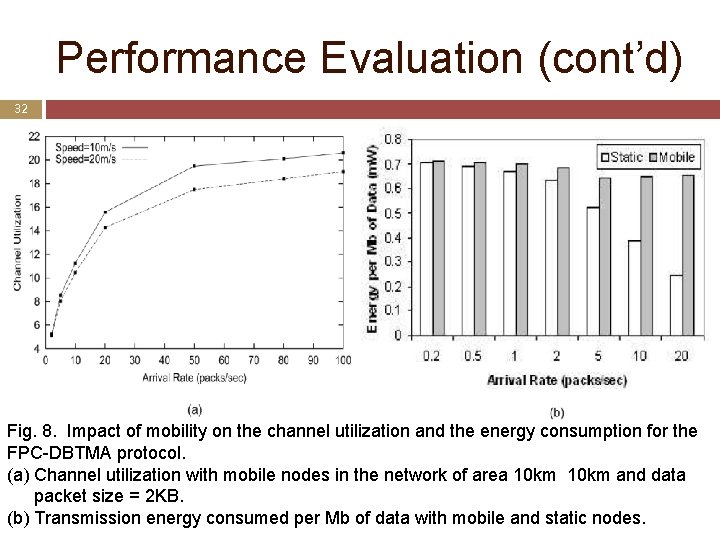
Performance Evaluation (cont’d) 32 Fig. 8. Impact of mobility on the channel utilization and the energy consumption for the FPC-DBTMA protocol. (a) Channel utilization with mobile nodes in the network of area 10 km and data packet size = 2 KB. (b) Transmission energy consumed per Mb of data with mobile and static nodes.
Performance Evaluation (cont’d) 33 Discussion of 5. Impact of mobility Higher speed causes a higher number of link drops Degrade Mobility the channel utilization costs more energy Frequent packet loss at high load
Conclusions 34 The global power-controlled protocol FPC-DBTMA in ad hoc networks for increasing the capacity of the networks Future work Not considered the effects of fast fading and other dynamic properties of the channel in this protocol Looking at time varying admission control and link protection algorithms, which can nullify the effect of mobility in ad hoc networks

Comments 35 Depict the protocol procedure step-by-step formally Clarify their objective of performance evaluation Different metrics and different situations For myself Insufficient knowledge of PHY and mathematical analysis (probability and linear algebra)
- Slides: 35