03 Introduction to Kernel UNIX Kernel Christian The

![memory instruction [Kernel mode] Add Sub Disk write Disk read Tape write Disable interrupt memory instruction [Kernel mode] Add Sub Disk write Disk read Tape write Disable interrupt](https://slidetodoc.com/presentation_image/af0c45cba15b7f3bd55da0d75433811d/image-13.jpg)
- Slides: 31

제 03강 : Introduction to Kernel UNIX Kernel Christian, The UNIX Operating System, 2 nd Ed, Wiley. Silberschatz, Galvin & Gagne, Applied Operating System Concepts, John Wiley & Sons Inc. 1

• Kernel – memory resident part of UNIX – majority written in C rest in assembler language (HW dependent, speed) – a. out (a plain C a. out program) – consists of functions • other programs can call (some of) these functions • called “system call function” – 3 parts • process management • file system • I/O system 2

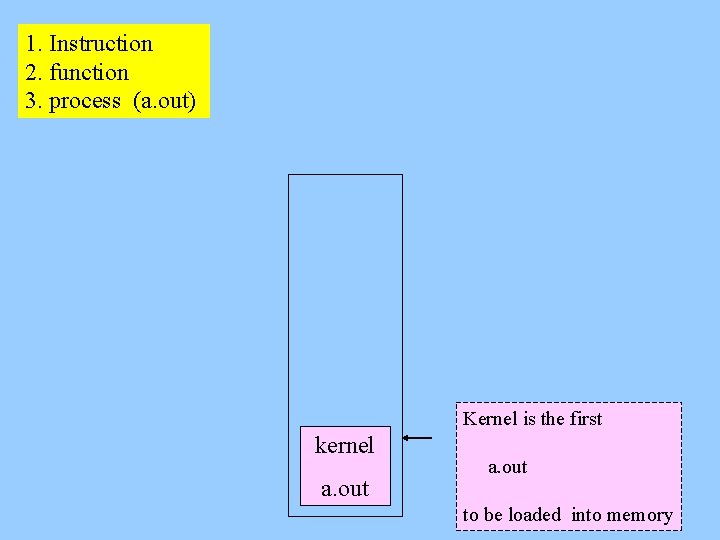
1. Instruction 2. function 3. process (a. out) Kernel is the first kernel a. out 3 to be loaded into memory

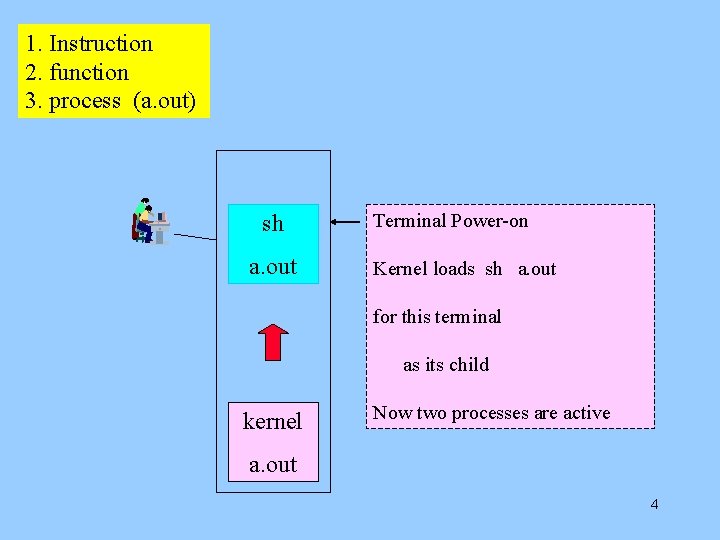
1. Instruction 2. function 3. process (a. out) sh a. out Terminal Power-on Kernel loads sh a. out for this terminal as its child kernel Now two processes are active a. out 4

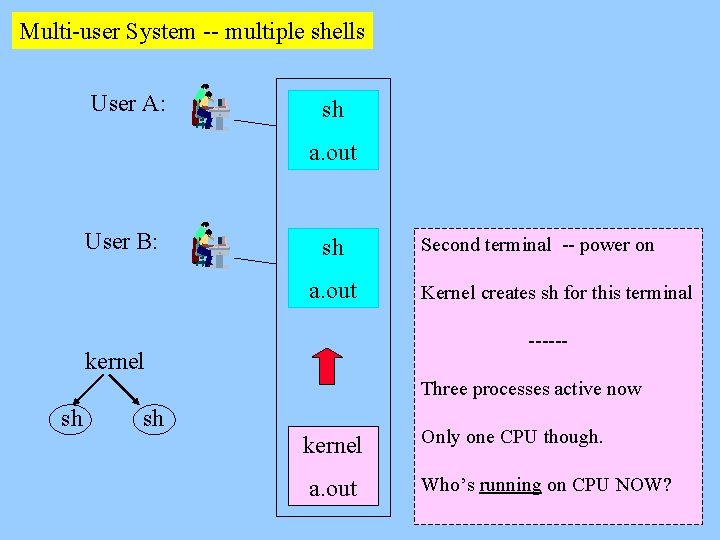
Multi-user System -- multiple shells User A: sh a. out User B: sh a. out Second terminal -- power on Kernel creates sh for this terminal ------ kernel Three processes active now sh sh kernel a. out Only one CPU though. Who’s running on CPU NOW? 5

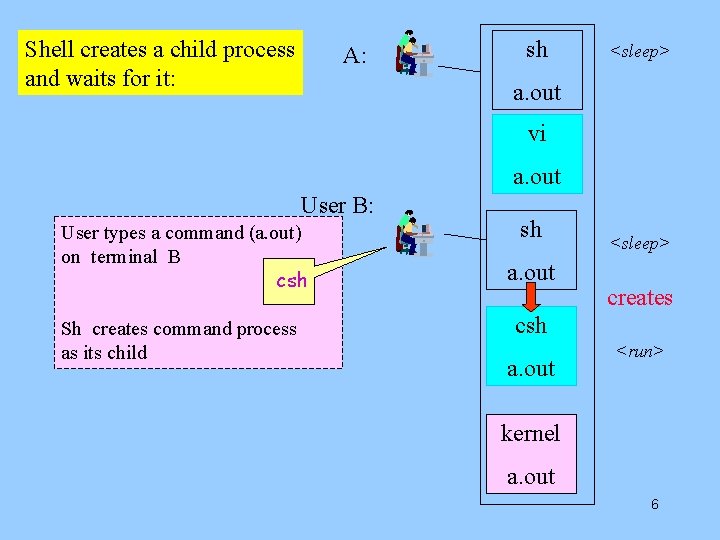
Shell creates a child process and waits for it: A: sh <sleep> a. out vi a. out User B: User types a command (a. out) on terminal B csh Sh creates command process as its child sh a. out <sleep> creates csh a. out <run> kernel a. out 6

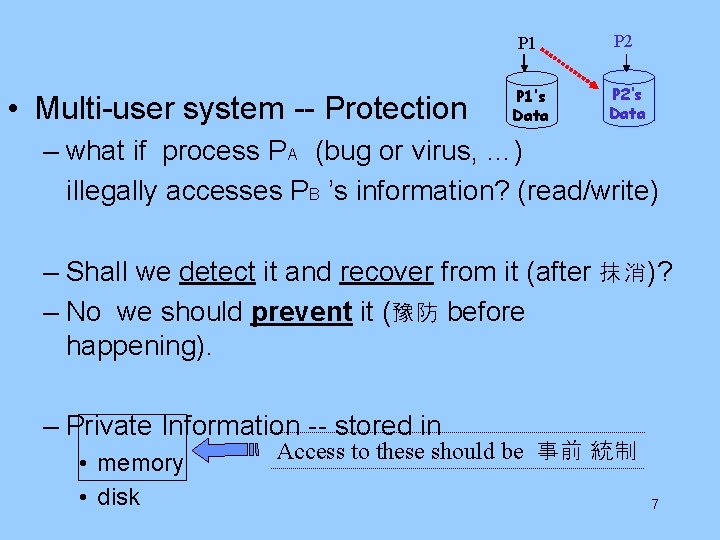
• Multi-user system -- Protection P 1 P 2 P 1’s Data P 2’s Data – what if process PA (bug or virus, …) illegally accesses PB ’s information? (read/write) – Shall we detect it and recover from it (after 抹消)? – No we should prevent it (豫防 before happening). – Private Information -- stored in • memory • disk Access to these should be 事前 統制 7

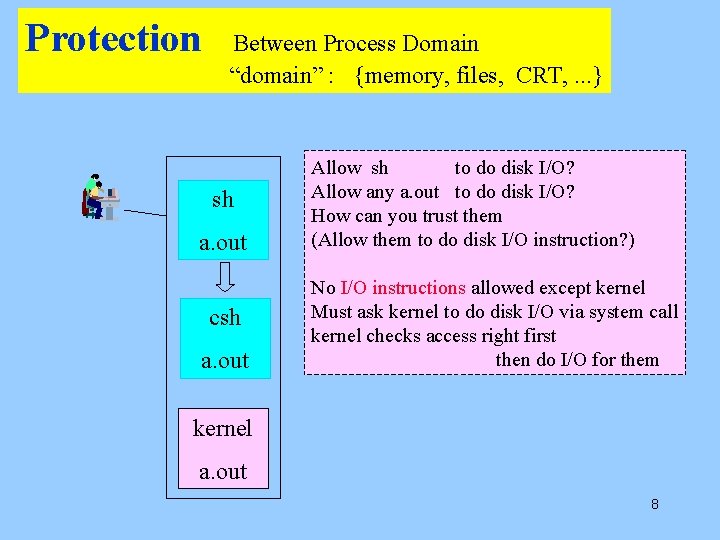
Protection Between Process Domain “domain” : {memory, files, CRT, . . . } sh a. out csh a. out Allow sh to do disk I/O? Allow any a. out to do disk I/O? How can you trust them (Allow them to do disk I/O instruction? ) No I/O instructions allowed except kernel Must ask kernel to do disk I/O via system call kernel checks access right first then do I/O for them kernel a. out 8

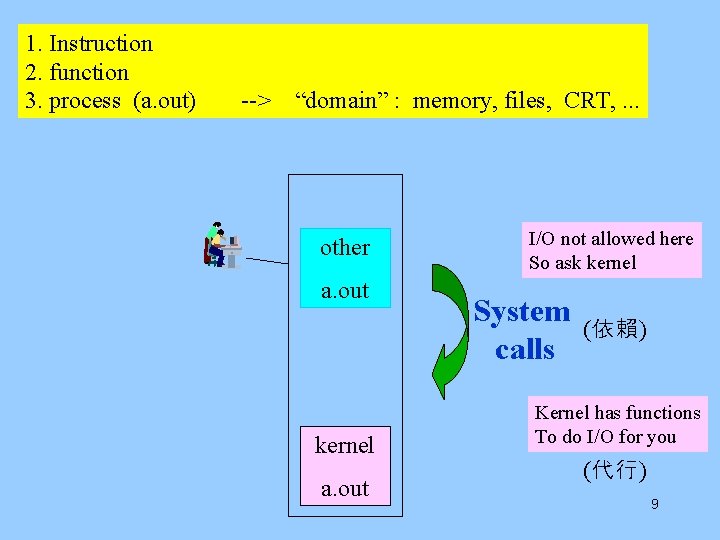
1. Instruction 2. function 3. process (a. out) --> “domain” : memory, files, CRT, . . . other a. out kernel a. out I/O not allowed here So ask kernel System calls (依賴) Kernel has functions To do I/O for you (代行) 9

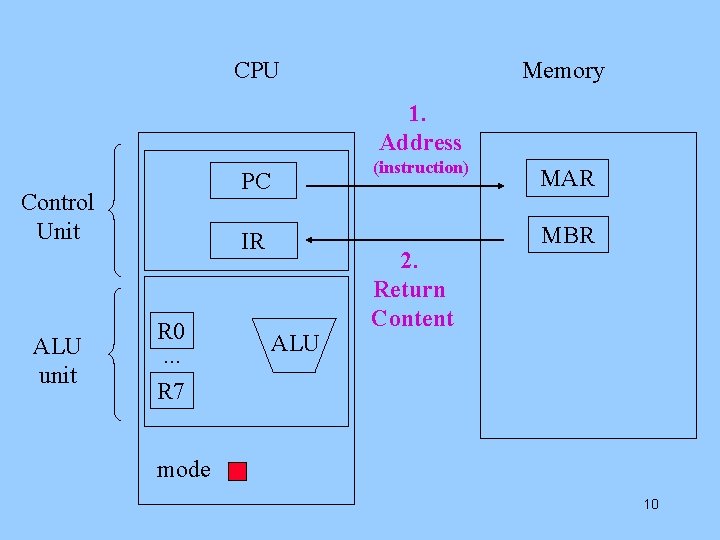
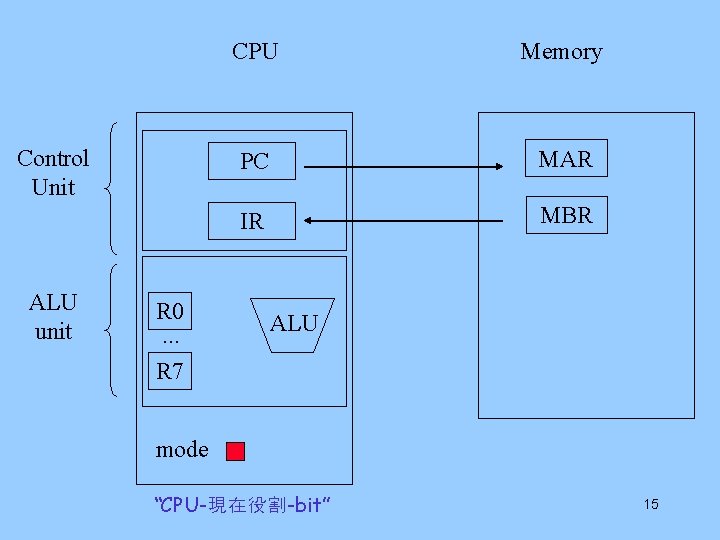
CPU Memory 1. Address PC Control Unit ALU unit (instruction) IR R 0. . . R 7 ALU 2. Return Content MAR MBR mode 10

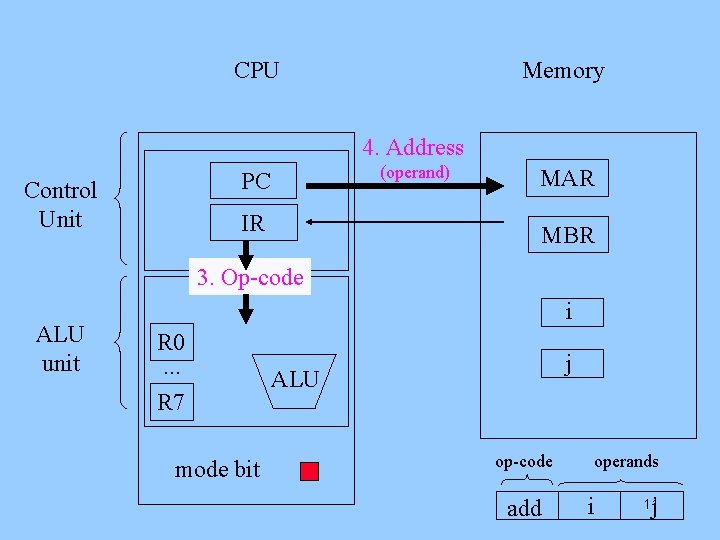
CPU Memory 4. Address (operand) PC Control Unit IR MAR MBR 3. Op-code ALU unit i R 0. . . R 7 mode bit j ALU op-code add operands i j 11

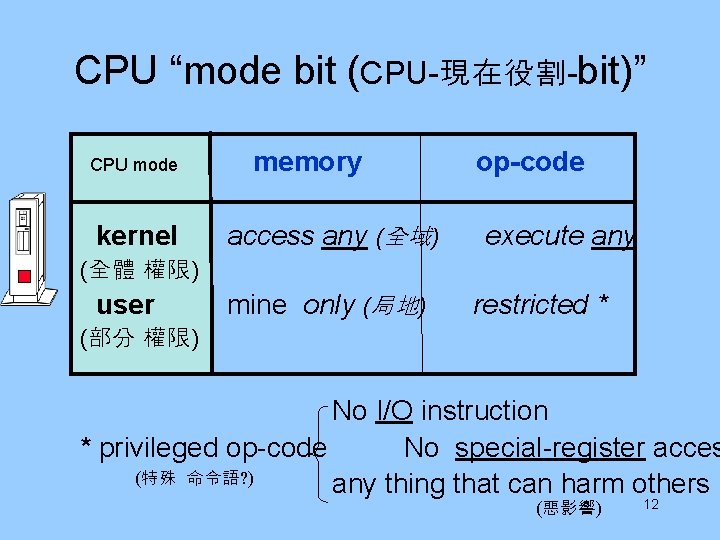
CPU “mode bit (CPU-現在役割-bit)” CPU mode kernel memory access any (全域) op-code execute any (全體 權限) user mine only (局地) restricted * (部分 權限) No I/O instruction * privileged op-code No special-register acces (特殊 命令語? ) any thing that can harm others (惡影響) 12
![memory instruction Kernel mode Add Sub Disk write Disk read Tape write Disable interrupt memory instruction [Kernel mode] Add Sub Disk write Disk read Tape write Disable interrupt](https://slidetodoc.com/presentation_image/af0c45cba15b7f3bd55da0d75433811d/image-13.jpg)
memory instruction [Kernel mode] Add Sub Disk write Disk read Tape write Disable interrupt Enable interrupt [User mode] a. out Add Sub Disk write Disk read Tape write Disable interrupt Enable interrupt 13

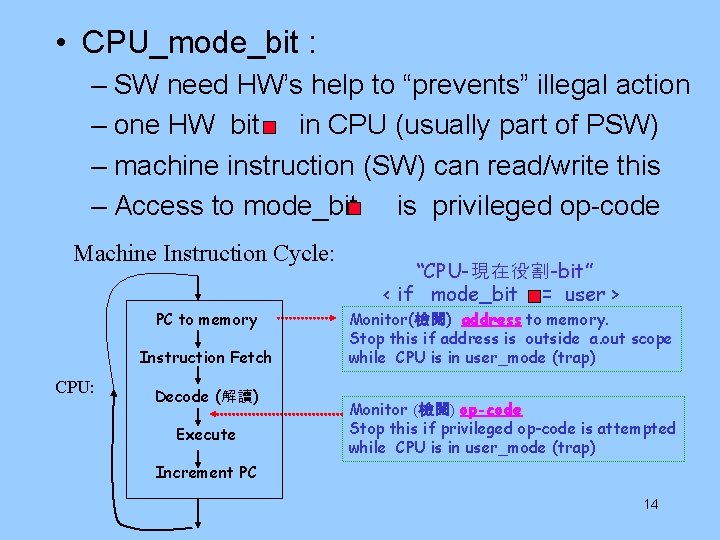
• CPU_mode_bit : – SW need HW’s help to “prevents” illegal action – one HW bit in CPU (usually part of PSW) – machine instruction (SW) can read/write this – Access to mode_bit is privileged op-code Machine Instruction Cycle: PC to memory Instruction Fetch CPU: Decode (解讀) Execute “CPU-現在役割-bit” < if mode_bit = user > Monitor(檢閱) address to memory. Stop this if address is outside a. out scope while CPU is in user_mode (trap) Monitor (檢閱) op-code Stop this if privileged op-code is attempted while CPU is in user_mode (trap) Increment PC 14

Control Unit ALU unit R 0. . . R 7 CPU Memory PC MAR IR MBR ALU mode “CPU-現在役割-bit” 15

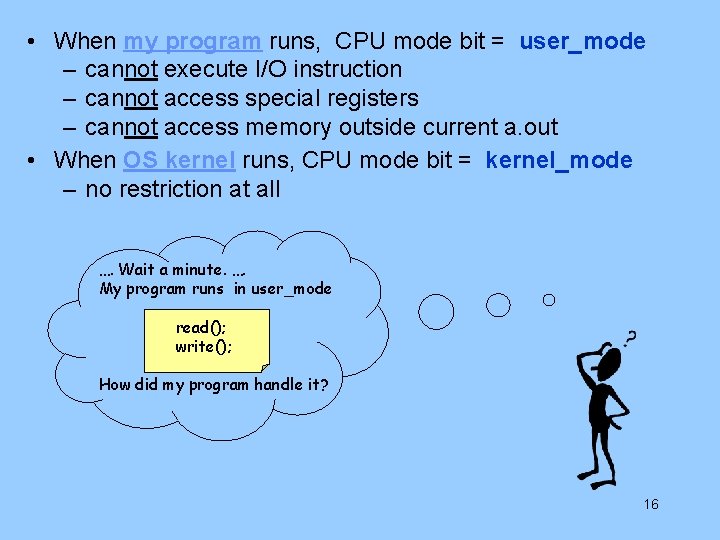
• When my program runs, CPU mode bit = user_mode – cannot execute I/O instruction – cannot access special registers – cannot access memory outside current a. out • When OS kernel runs, CPU mode bit = kernel_mode – no restriction at all …. Wait a minute. …. My program runs in user_mode read(); write(); How did my program handle it? 16

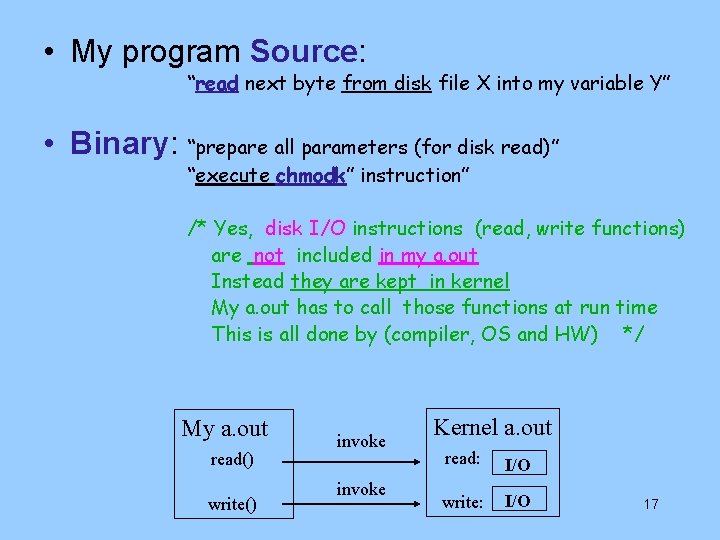
• My program Source: “read next byte from disk file X into my variable Y” • Binary: “prepare all parameters (for disk read)” “execute chmodk” instruction” /* Yes, disk I/O instructions (read, write functions) are not included in my a. out Instead they are kept in kernel My a. out has to call those functions at run time This is all done by (compiler, OS and HW) */ My a. out read() write() invoke Kernel a. out read: I/O write: I/O 17

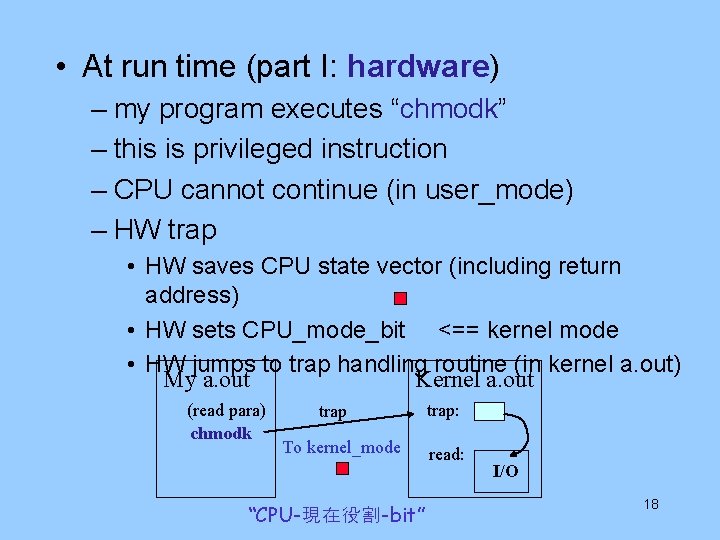
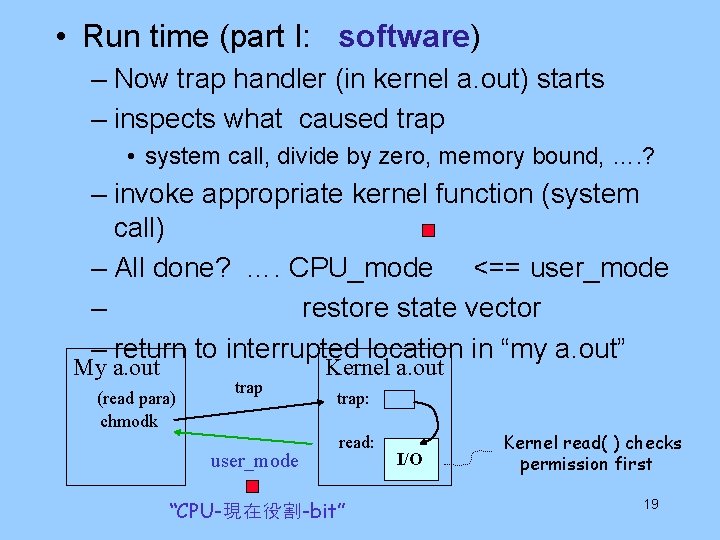
• At run time (part I: hardware) – my program executes “chmodk” – this is privileged instruction – CPU cannot continue (in user_mode) – HW trap • HW saves CPU state vector (including return address) • HW sets CPU_mode_bit <== kernel mode • HW jumps to trap handling routine (in kernel a. out) My a. out Kernel a. out (read para) chmodk trap To kernel_mode “CPU-現在役割-bit” trap: read: I/O 18

• Run time (part I: software) – Now trap handler (in kernel a. out) starts – inspects what caused trap • system call, divide by zero, memory bound, …. ? – invoke appropriate kernel function (system call) – All done? …. CPU_mode <== user_mode – restore state vector – return to interrupted location in “my a. out” My a. out (read para) chmodk trap user_mode Kernel a. out trap: read: “CPU-現在役割-bit” I/O Kernel read( ) checks permission first 19

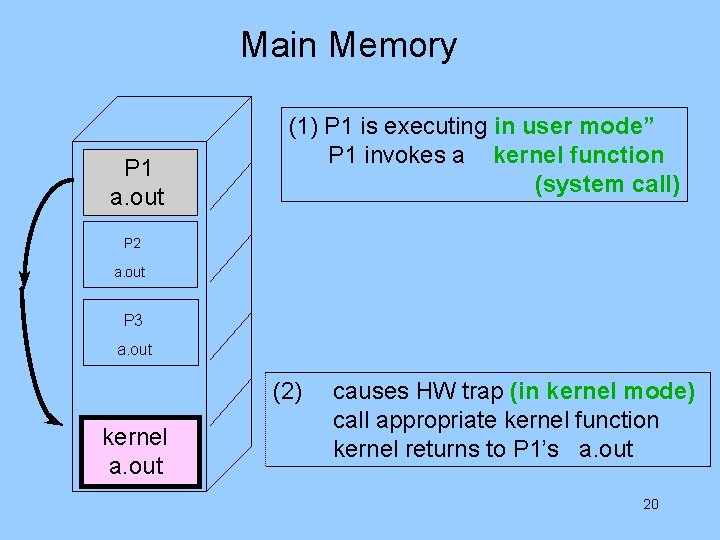
Main Memory P 1 a. out (1) P 1 is executing in user mode” P 1 invokes a kernel function (system call) P 2 a. out P 3 a. out (2) kernel a. out causes HW trap (in kernel mode) call appropriate kernel function kernel returns to P 1’s a. out 20

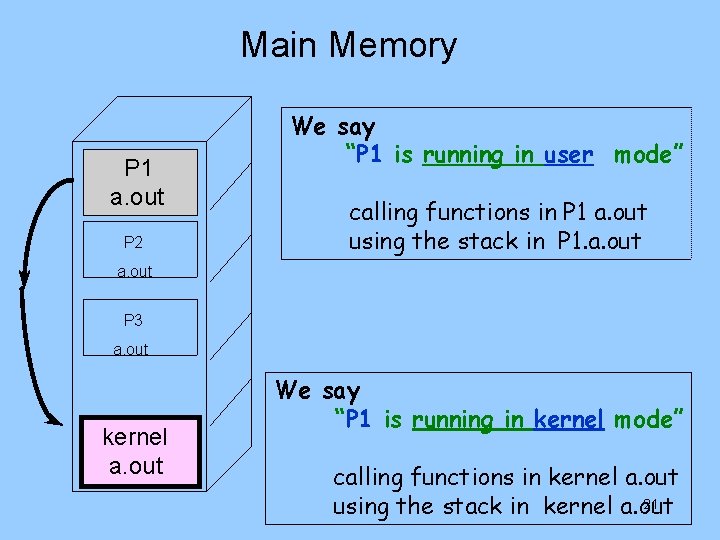
Main Memory P 1 a. out P 2 We say “P 1 is running in user mode” calling functions in P 1 a. out using the stack in P 1. a. out P 3 a. out kernel a. out We say “P 1 is running in kernel mode” calling functions in kernel a. out 21 using the stack in kernel a. out

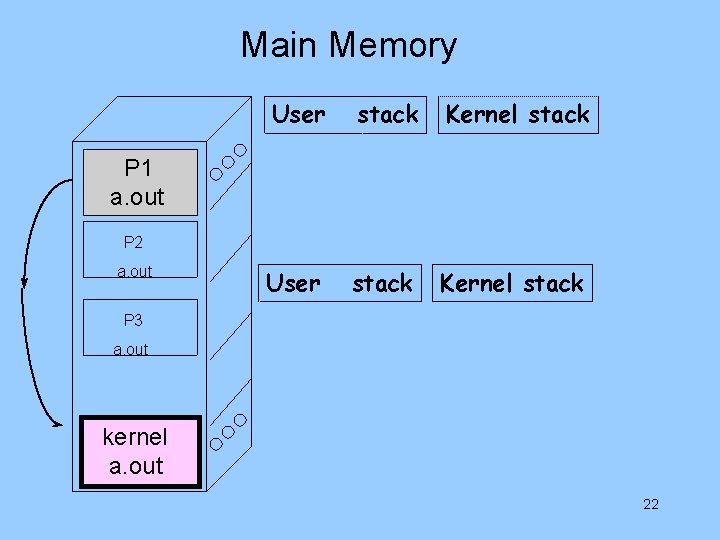
Main Memory User stack Kernel stack P 1 a. out P 2 a. out P 3 a. out kernel a. out 22

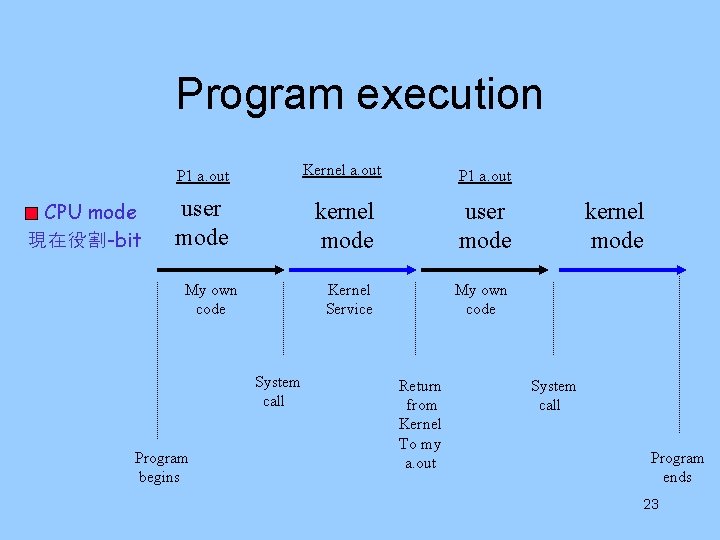
Program execution CPU mode 現在役割-bit P 1 a. out Kernel a. out P 1 a. out user mode kernel mode user mode Kernel Service My own code System call Program begins Return from Kernel To my a. out kernel mode System call Program ends 23

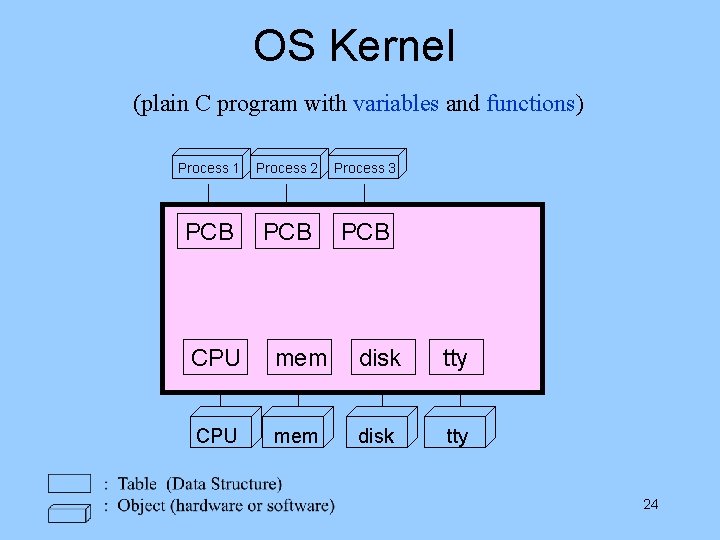
OS Kernel (plain C program with variables and functions) Process 1 Process 2 Process 3 PCB PCB CPU mem disk tty 24

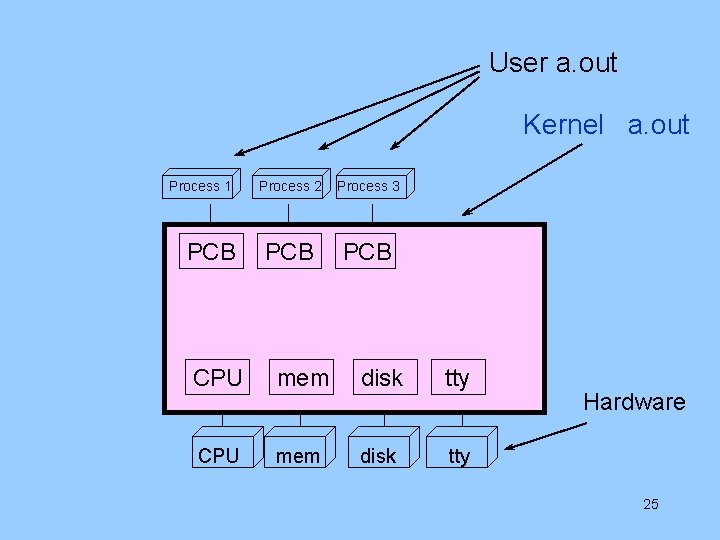
User a. out Kernel a. out Process 1 PCB Process 2 Process 3 PCB CPU mem disk tty Hardware 25

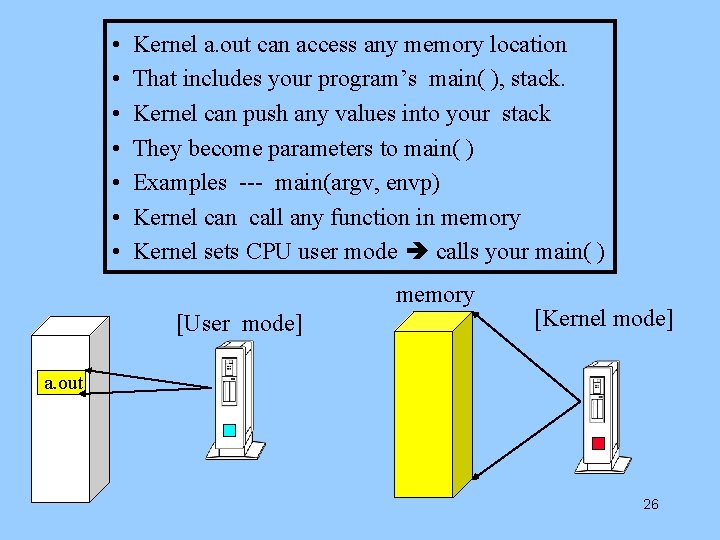
• • Kernel a. out can access any memory location That includes your program’s main( ), stack. Kernel can push any values into your stack They become parameters to main( ) Examples --- main(argv, envp) Kernel can call any function in memory Kernel sets CPU user mode calls your main( ) memory [User mode] [Kernel mode] a. out 26

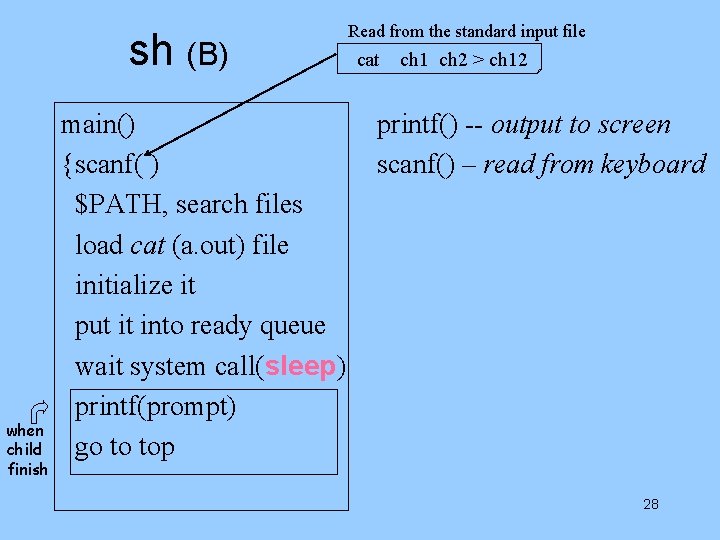
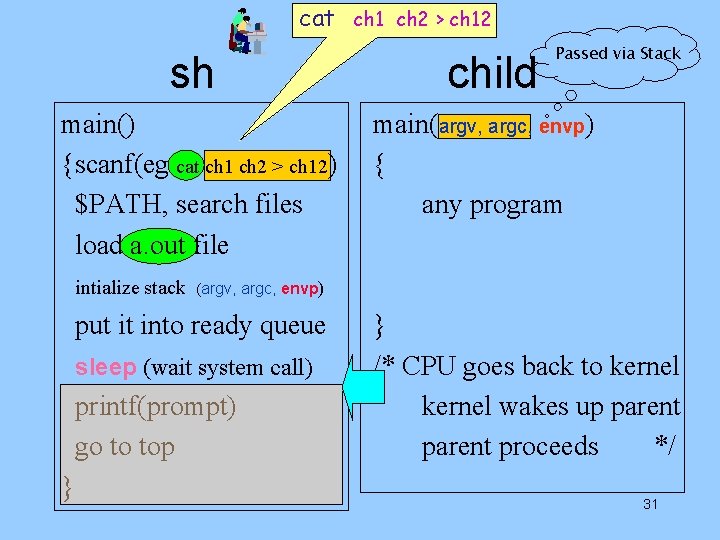
Second shell runs: User A: sh a. out cat ch 1 ch 2 > ch 12 cat User B: sh kernel sh sh a. out vi cat kernel a. out <sleep> <run> 27

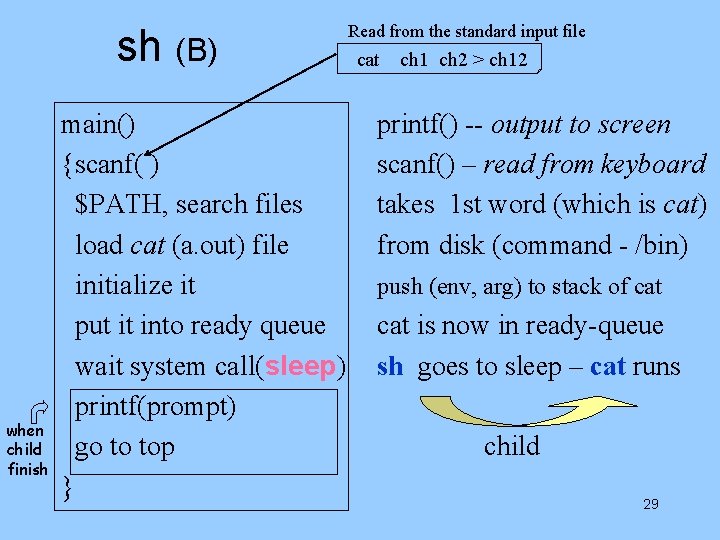
sh (B) when child finish main() {scanf( ) $PATH, search files load cat (a. out) file initialize it put it into ready queue wait system call(sleep) printf(prompt) go to top Read from the standard input file cat ch 1 ch 2 > ch 12 printf() -- output to screen scanf() – read from keyboard 28

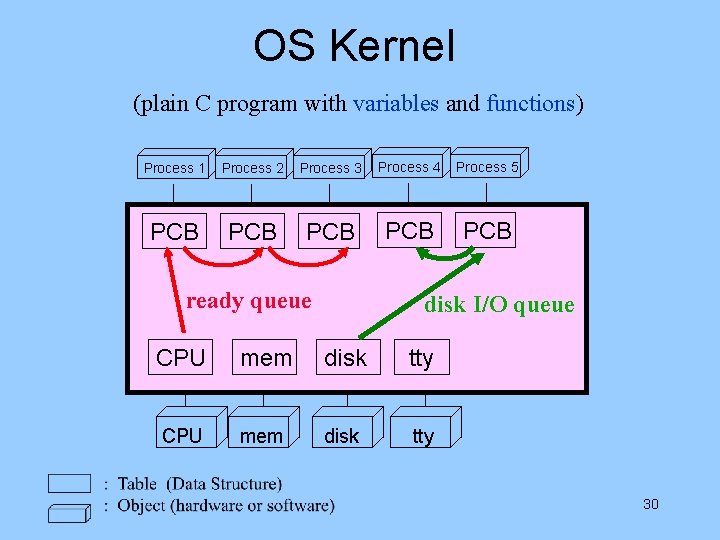
sh (B) when child finish main() {scanf( ) $PATH, search files load cat (a. out) file initialize it put it into ready queue wait system call(sleep) printf(prompt) go to top } Read from the standard input file cat ch 1 ch 2 > ch 12 printf() -- output to screen scanf() – read from keyboard takes 1 st word (which is cat) from disk (command - /bin) push (env, arg) to stack of cat is now in ready-queue sh goes to sleep – cat runs child 29

OS Kernel (plain C program with variables and functions) Process 1 Process 2 Process 3 Process 4 Process 5 PCB PCB PCB ready queue disk I/O queue CPU mem disk tty 30

cat ch 1 ch 2 > ch 12 sh main() {scanf(eg cat ch 1 ch 2 > ch 12) $PATH, search files load a. out file intialize stack main(argv, argc, envp) { any program (argv, argc, envp) put it into ready queue sleep (wait system call) printf(prompt) go to top } child Passed via Stack } /* CPU goes back to kernel wakes up parent proceeds */ 31